Last year, we profiled a Mac trojan horse known as "Flashback" that was masquerading as a Flash Player installer. While Apple has taken steps to protect users from the threat using its File Quarantine system under which users' computers initiate daily checks for updated malware definitions, the malware's authors have continued to tweak the trojan to improve its ability to both infect systems and evade detection.
Security firm Intego has issued a report on a new variant of the trojan, known as Flashback.G, which adopts a multi-pronged strategy in attacking users' systems. The first two methods rely on vulnerabilities in Java, and while the vulnerabilities are patched in systems running up-to-date versions of Java, outdated systems can be silently infected through these security holes.
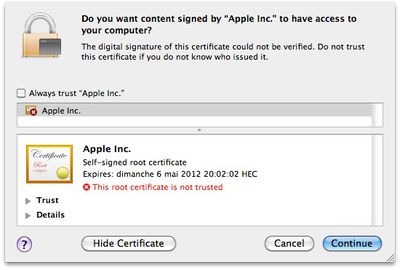
Flashback.G's self-signed certificate seeking to trick users into allowing installation
On up-to-date systems lacking the Java vulnerabilities, Flashback.G presents a self-signed certificate claiming to be from Apple in an attempt to fool users into allowing the trojan to be installed on their systems. Once installed, the trojan begins searching for user names and passwords it can relay to the malware's authors.
This malware patches web browsers and network applications essentially to search for user names and passwords. It looks for a number of domains – websites such as Google, Yahoo!, CNN; bank websites; PayPal; and many others. Presumably, the people behind this malware are looking for both user names and passwords that they can immediately exploit – such as for a bank website – as well as others that may be reused on different sites.
Notably, Intego reports that the trojan aborts its own installation if it detects the presence of any of several antivirus applications on a user's Mac, presumably seeking to remain below the radar while focusing on vulnerable systems.
Intego recommends that users on Mac OS X Snow Leopard make sure that Java is fully up-to-date by running a check through Software Update, and for all users to be aware of the social engineering trick the trojan uses in attempting to gain permission for installation. The company of course also recommends that users equip their systems with antivirus software.
While malware has not been a tremendous threat to Mac users so far, its presence has been growing. Apple has stepped up its efforts to combat malware by enhancing its File Quarantine system to provide for the daily definition checks. OS X Mountain Lion will see another significant step with the introduction of Gatekeeper, a system by which users can limit installation of apps to sources such as the Mac App Store and developers who have registered with Apple as "identified developers".
Apple's Developer-ID program will utilize digital signatures on applications to link applications with a specific developer. If the developer is later discovered to be distributing malware or otherwise behaving improperly, installations of its existing apps can be deactivated by Gatekeeper. Gatekeeper does have its limitations, however, as it only scans applications downloaded through a handful of mechanisms such as browsers and can not detect applications that are modified by malware after their initial launch.