Alleged iOS Security Flaw Enables Malicious Apps to Secretly Log User Touch Inputs
Researchers from security firm FireEye have revealed a new bug in iOS that enables a malicious app to monitor and log a user's touch inputs and button uses while running in the background, reports Ars Technica. The exploit reportedly targets a flaw in iOS' multitasking capabilities to capture user inputs, and allows for them to be sent to a remote server.
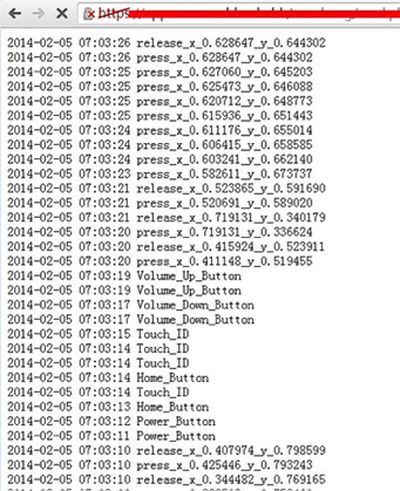
To demonstrate the flaw, the researchers created a proof-of-concept monitoring app and developed approaches to "bypass" Apple's App Store Review process effectively. Once the app was installed on an iOS device, actions including keyboard inputs, use of the volume, home, and power buttons, screen touches with exact coordinates, and Touch ID events were all captured. The researchers also noted that disabling iOS 7's "Background App Refresh" setting would not disable a malicious app from logging data, as the only present solution to the problem is to manually remove apps from the task switcher.
FireEye also spoke about the flaw being identified in current versions of iOS:
Note that the demo exploits the latest 7.0.4 version of iOS system on a non-jailbroken iPhone 5s device successfully. We have verified that the same vulnerability also exists in iOS versions 7.0.5, 7.0.6 and 6.1.x. Based on the findings, potential attackers can either use phishing to mislead the victim to install a malicious/vulnerable app or exploit another remote vulnerability of some app, and then conduct background monitoring.
The group added that it is actively working with Apple on the issue, although the company has yet to comment publicly. The news comes less than a week after Apple issued iOS 7.0.6 in response to a SSL vulnerability that allowed a hacker to capture or modify data from Safari in supposedly secure sessions.
The SSL security bug was also found to be present in OS X, as new research over the weekend revealed that additional apps such as FaceTime and iMessage could be compromised. Apple confirmed to Reuters that it will issue an OS X software update "very soon" to patch the bug.
Popular Stories
An iPhone 17 announcement is a dead cert for September 2025 – Apple has already sent out invites for an "Awe dropping" event on Tuesday, September 9 at the Apple Park campus in Cupertino, California. The timing follows Apple's trend of introducing new iPhone models annually in the fall.
At the event, Apple is expected to unveil its new-generation iPhone 17, an all-new ultra-thin iPhone 17...
Apple is expected to unveil the iPhone 17 series on Tuesday, September 9, and last-minute rumors about the devices continue to surface.
The latest info comes from a leaker known as Majin Bu, who has shared alleged images of Apple's Clear Case for the iPhone 17 Pro and Pro Max, or at least replicas.
Image Credit: @MajinBuOfficial
The images show three alleged changes compared to Apple's iP...
Apple and Samsung have reportedly issued cease-and-desist notices to Xiaomi in India for an ad campaign that directly compares the rivals' devices to Xiaomi's products. The two companies have threatened the Chinese vendor with legal action, calling the ads "disparaging."
Ads have appeared in local print media and on social media that take pot shots at the competitors' premium offerings. One...
Apple will launch its new iPhone 17 series this month, and the iPhone 17 Pro models are expected to get a new design for the rear casing and the camera area. But more significant changes to the lineup are not expected until next year, when the iPhone 18 models arrive.
If you're thinking of trading in your iPhone for this year's latest, consider the following features rumored to be coming to...
Apple is preparing to release iOS 18.7 for compatible iPhone models, according to evidence of the update in the MacRumors visitor logs.
We expect iOS 18.7 to be released in September, alongside iOS 26. The update will likely include fixes for security vulnerabilities, but little else.
iOS 18.7 will be one of the final updates ever released for the iPhone XS, iPhone XS Max, and iPhone XR,...



















